Every email you send, video call you make or website you load involves a complex sequence of data exchanges between systems. While much of this happens invisibly, there’s a model that helps explain how it all works: the OSI model. Short for Open Systems Interconnection, the OSI model is a theoretical framework developed by the International Organization for Standardization (ISO) to standardize how data moves through a network.
Even though today’s internet primarily uses the more streamlined TCP/IP model, the OSI model remains foundational in education, cybersecurity and network management. Understanding it helps businesses pinpoint network issues, make informed security decisions and recognize where cyber threats might strike.
Table of contents
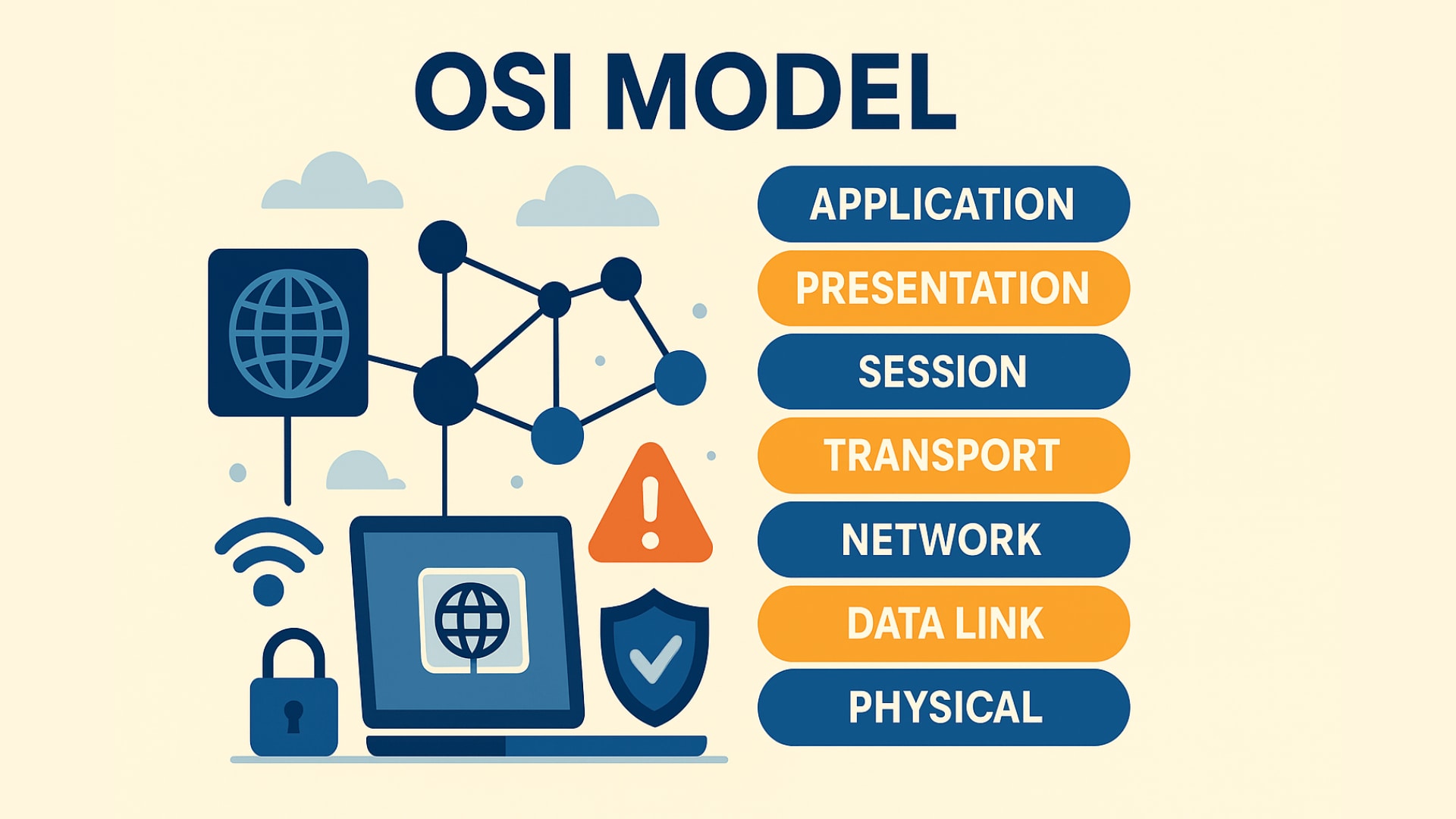
The Seven Layers of the OSI Model Explained
The OSI model breaks down communication between systems into seven distinct layers. Each layer serves a specific function and interacts only with its immediate neighbors.
Layer 7: Application Layer
This is the closest layer to the end-user. It enables software applications — like web browsers, email clients and messaging apps — to interact with the network. Protocols like HTTP, FTP and SMTP operate at this level. It’s also a frequent target for cyberattacks, including phishing, cross-site scripting (XSS) and form abuse. Attackers often exploit this layer because it interacts directly with users, making it a gateway for social engineering and bot-based attacks.
Layer 6: Presentation Layer
Here, data is prepared for application use. It translates between different data formats, handles data encryption and decryption and performs compression when needed. Secure connections — like those using HTTPS — rely on this layer to decode encrypted transmissions. Without this layer, communication between different systems with varying formats would be difficult or impossible.
Layer 5: Session Layer
This layer manages the sessions or conversations between devices. It ensures that communication remains open as long as needed and properly closes the session afterward. It also supports features like checkpointing to recover from dropped connections. In cybersecurity, this layer plays a role in detecting session hijacking and ensuring session integrity.
Layer 4: Transport Layer
Responsible for delivering data across networks, this layer breaks data into segments, ensures error-free delivery and reassembles it on the receiving end. TCP (Transmission Control Protocol) provides reliable delivery through acknowledgments and retransmission, while UDP (User Datagram Protocol) offers faster delivery without confirmation. Attacks like TCP SYN floods exploit this layer to overwhelm systems.
Layer 3: Network Layer
This layer determines the best path for data to travel across multiple networks. It handles logical addressing using IP addresses and breaks data into packets. Routers operate primarily at this layer. Threats at this level include IP spoofing and route hijacking, which can mislead traffic or expose systems to man-in-the-middle attacks.
Layer 2: Data Link Layer
Concerned with node-to-node communication on the same network, this layer breaks packets into frames and manages error detection and correction for data transmitted over physical links. It uses MAC addresses to identify devices. ARP spoofing and MAC flooding are common Layer 2 attacks, often used to gain access to restricted areas of a network.
Layer 1: Physical Layer
This is the foundational layer, dealing with the actual hardware: cables, switches and radio signals. It converts data into electrical, optical, or radio signals and defines how bits are transmitted over a physical medium. Cable tampering, jamming wireless signals, or hardware-based data interception are threats relevant at this level.
Why the OSI Model Matters for Cybersecurity
Understanding the OSI model isn’t just academic. Each layer is a potential target for cyber threats. For example, DDoS attacks might overwhelm a server at Layer 7 (Application), while man-in-the-middle attacks can exploit vulnerabilities in Layers 4 and 6, where data is transported and encrypted.
Security tools are often aligned with specific OSI layers. Firewalls typically operate at Layers 3 and 4, filtering traffic based on IP addresses and ports. VPNs work at Layer 3, encrypting all data traveling between networks. Meanwhile, SSL/TLS protocols protect Layers 4 and 6, encrypting sensitive information during transmission.
For businesses, this model helps:
- Diagnose issues: Is a problem in your physical connection, or is an application failing to communicate?
- Implement the right security tools: Understanding the layers helps IT teams deploy defenses where they are most needed.
- Identify attack types: Different attacks target different layers. Knowing which layer is affected accelerates response times.
Applying OSI Knowledge in Business
The OSI model is especially useful for business environments with layered security strategies. If your team understands that malware might infiltrate through an unsecured application at Layer 7, you can better justify investments in application-level firewalls or CAPTCHAs. If you’re facing issues with unreliable connections, examining Layers 1 through 3 can help trace hardware or routing issues.
Layered understanding also supports compliance. For example, GDPR and similar regulations emphasize encryption and data security. Knowing how and where data is encrypted (Layers 4 and 6) ensures your practices meet legal requirements.
Beyond security, the OSI model helps optimize performance. Network engineers can pinpoint inefficiencies—whether due to slow application response times at Layer 7 or overloaded switches at Layer 1—and optimize accordingly.
OSI and the Role of CAPTCHAs
Since the Application Layer (Layer 7) is where users and services interact, it’s also the most visible and frequently targeted point in network communication. Automated attacks, such as fake sign-ups, credential stuffing and spam submissions, primarily occur at this layer.
To combat these threats, CAPTCHA solutions are deployed to differentiate human users from bots. CAPTCHAs act as a gatekeeper at Layer 7, analyzing user behavior, detecting patterns consistent with automation and blocking access to critical endpoints when necessary.
Modern CAPTCHA solutions like those offered by captcha.eu enhance this layer’s defense without compromising usability. Using cryptographic proof-of-work and anonymized behavioral signals, captcha.eu ensures bots are filtered out while human users enjoy a smooth, privacy-respecting experience. Unlike legacy systems that rely on intrusive image challenges or personal tracking, captcha.eu’s solution operates seamlessly within GDPR frameworks and WCAG accessibility standards, making it ideal for businesses prioritizing both security and user experience.
Conclusion
While the OSI model may seem theoretical, it has very real applications in modern cybersecurity and IT infrastructure. Each layer represents a point of vulnerability — and opportunity — for network defense. For businesses navigating digital growth and security threats, understanding the OSI model equips teams to design better systems, troubleshoot smarter and protect more effectively.
From the cables in your server room to the applications your users rely on, the OSI model explains how it all fits together. And when it comes to defending the Application Layer from bot abuse, a well-placed CAPTCHA solution — like those offered by captcha.eu — can make all the difference.
FAQ – Frequently Asked Questions
What is the OSI Model in simple terms?
The OSI Model is a framework that explains how data travels across a network. It breaks the process into seven layers, from physical hardware (like cables) to the software applications users interact with. Each layer has a specific role in sending and receiving data.
Why is the OSI Model important in cybersecurity?
The OSI Model helps security teams identify where specific attacks occur and apply appropriate defenses. For example, firewalls operate at lower layers (3 and 4), while CAPTCHAs work at the Application Layer (7) to block bots and automated abuse.
What are the seven layers of the OSI Model?
Physical – Transmits raw data via cables or wireless signals.
Data Link – Manages direct connections between devices on the same network.
Network – Routes data between networks using IP addresses.
Transport – Ensures reliable delivery of data segments.
Session – Manages ongoing communication sessions.
Presentation – Translates and encrypts data for use by applications.
Application – Interfaces directly with the end user’s software.
How does the OSI Model help in troubleshooting?
By isolating network issues to a specific layer (e.g., checking cable connections at Layer 1 or verifying IP routes at Layer 3), IT teams can diagnose and resolve problems more efficiently.
How do CAPTCHAs relate to the OSI Model?
CAPTCHAs operate at the Application Layer (Layer 7) to detect and block bots before they can access or abuse online services. They protect user-facing systems like login forms, registration pages, and comment sections.
100 free requests
You have the opportunity to test and try our product with 100 free requests.
If you have any questions
Contact us
Our support team is available to assist you.